
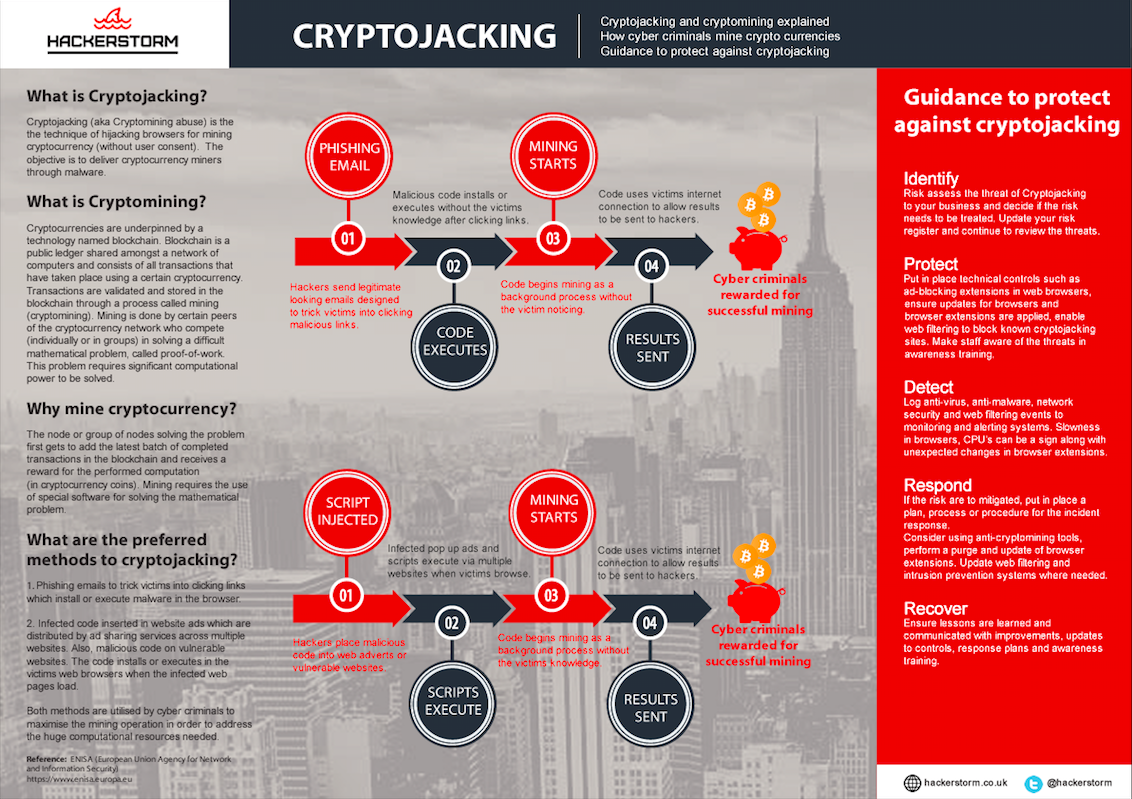
CRYPTOJACKING
The hijacking of web browsers and computers via malware to mine crypto-currencies such as bitcoin.

SANS & CIS Top 20 - Historical Timeline
How the controls have evolved over time and what does the future hold for the list.
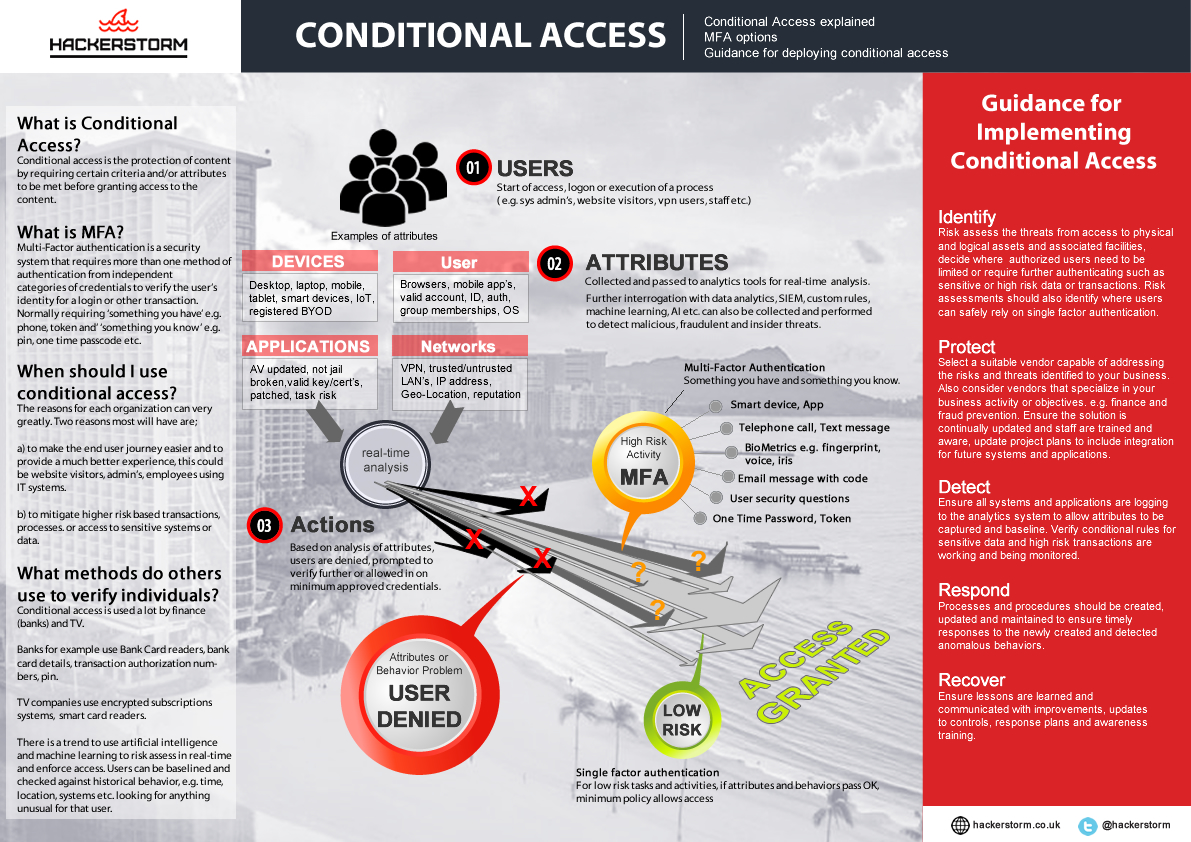
Access Control
Conditional Access & Multi Factor Authentication
ISO 27001/2 : A.9.1, A.9.2, A.9.3, A.9.4
NIST 800-53: AC1, IA Family
CIS Top 20: 4, 6, 14, 16
NCSC: Cyber Essentials 2, 3
NIST CSF: Protect PR.AC
Logging & Monitoring
Security weakness and vulnerability logging with Splunk
ISO 27001/2 : A.9, A.12.4, A.12.6, A.12.7, A.14, A.15.2, A.16.1, A.18.2
NIST 800-53: AU - Audit and Accountably Family (AU-1 to 16)
CIS Top 20: 3, 5, 11, 12, 19, 20
NIST CSF: Protect PR.PT-1, DE.AE, DE.CM, DE.DP

The section will have infographics explaining various types of cyber threats. Please check back for updates or follow us on twitter @hackerstorm
Click the images to view the info!.
Security Operations
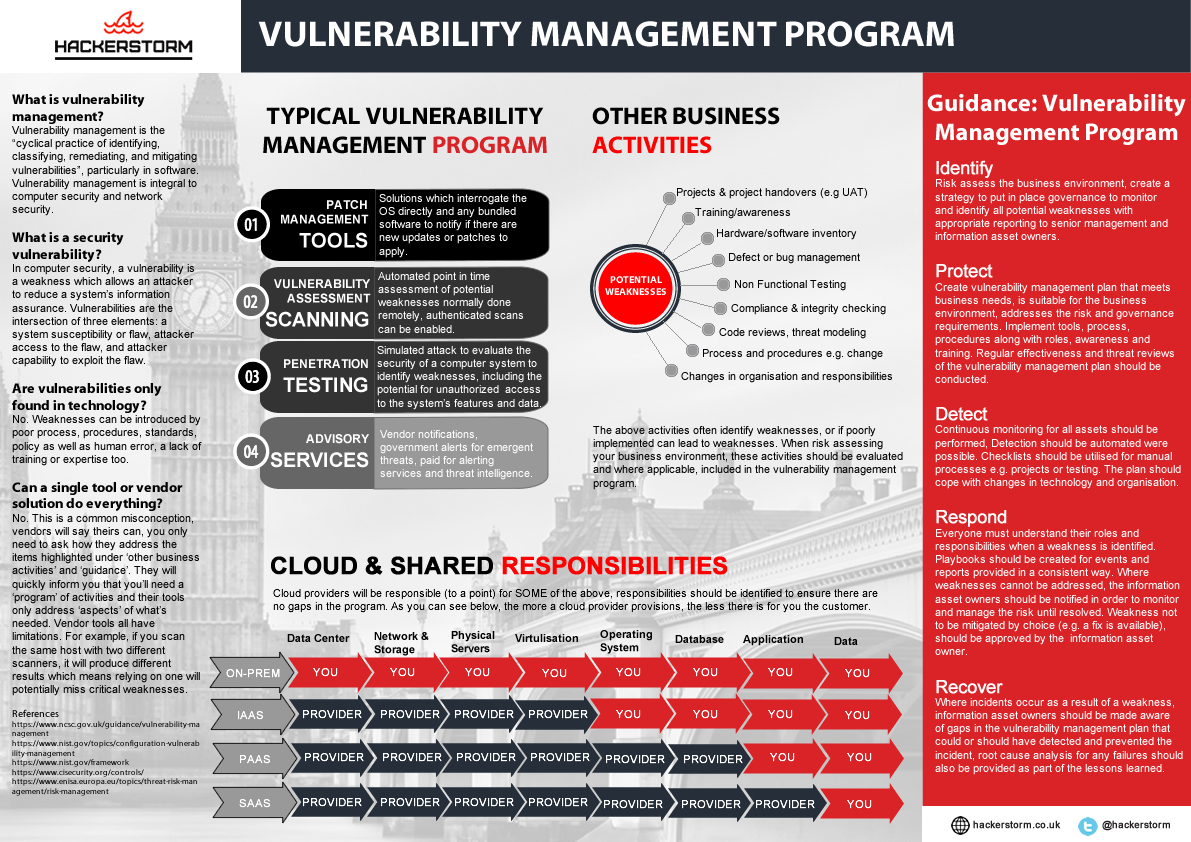
Vulnerability Management Program
ISO 27001/2 : A.12.6, A.14, 18.2
NIST 800-53: CM, CA-2, CA-7, RA-3, RA-5, SI-2, SI-5
CIS Top 20: 2, 5, 9, 11, 12, 14, 18, 20
NCSC: Cyber Essentials 2, 5
NIST CSF: ID.AM, PR.IP, DE.AE, DE.CM, RS.CO, RS.AN, RC.IM
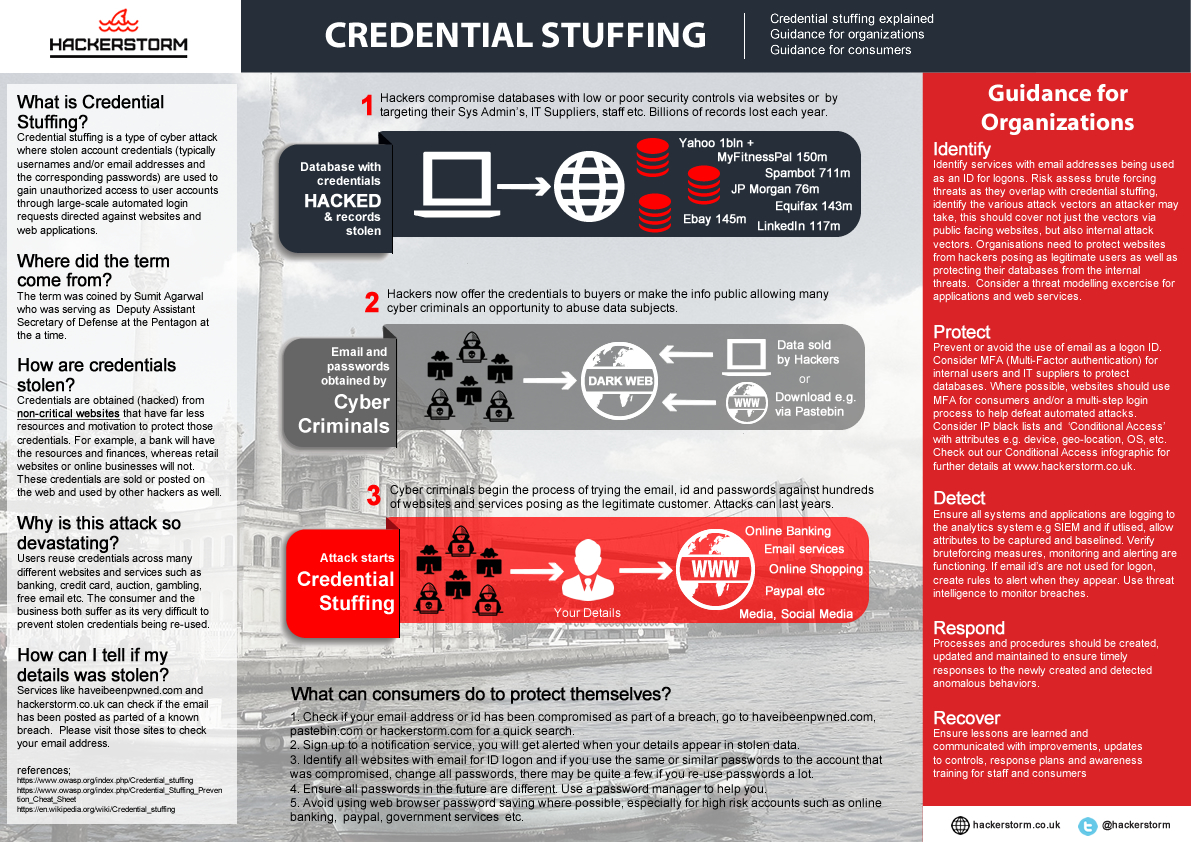
CREDENTIAL STUFFING
An automated attack used by Cyber Criminals which utlises stolen email, id and passwords from data breaches to logon as legitimate users. A devastating attack for both consumer and website owners
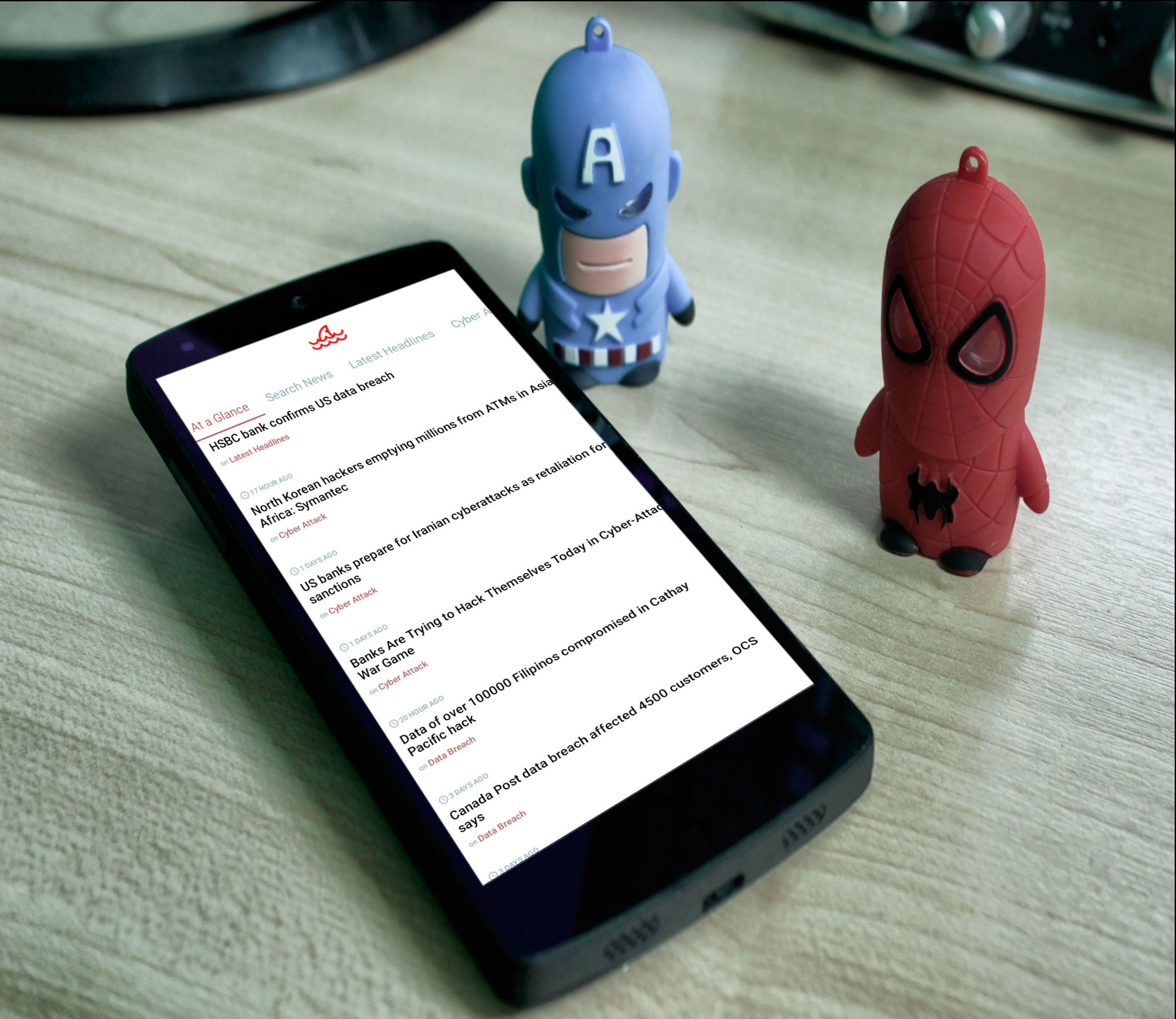
HackerStorm Cyber Security News App

Download our Security News App


Infographics - How To Guides
Our Free Apps
Infographics - Cyber Threats Guides
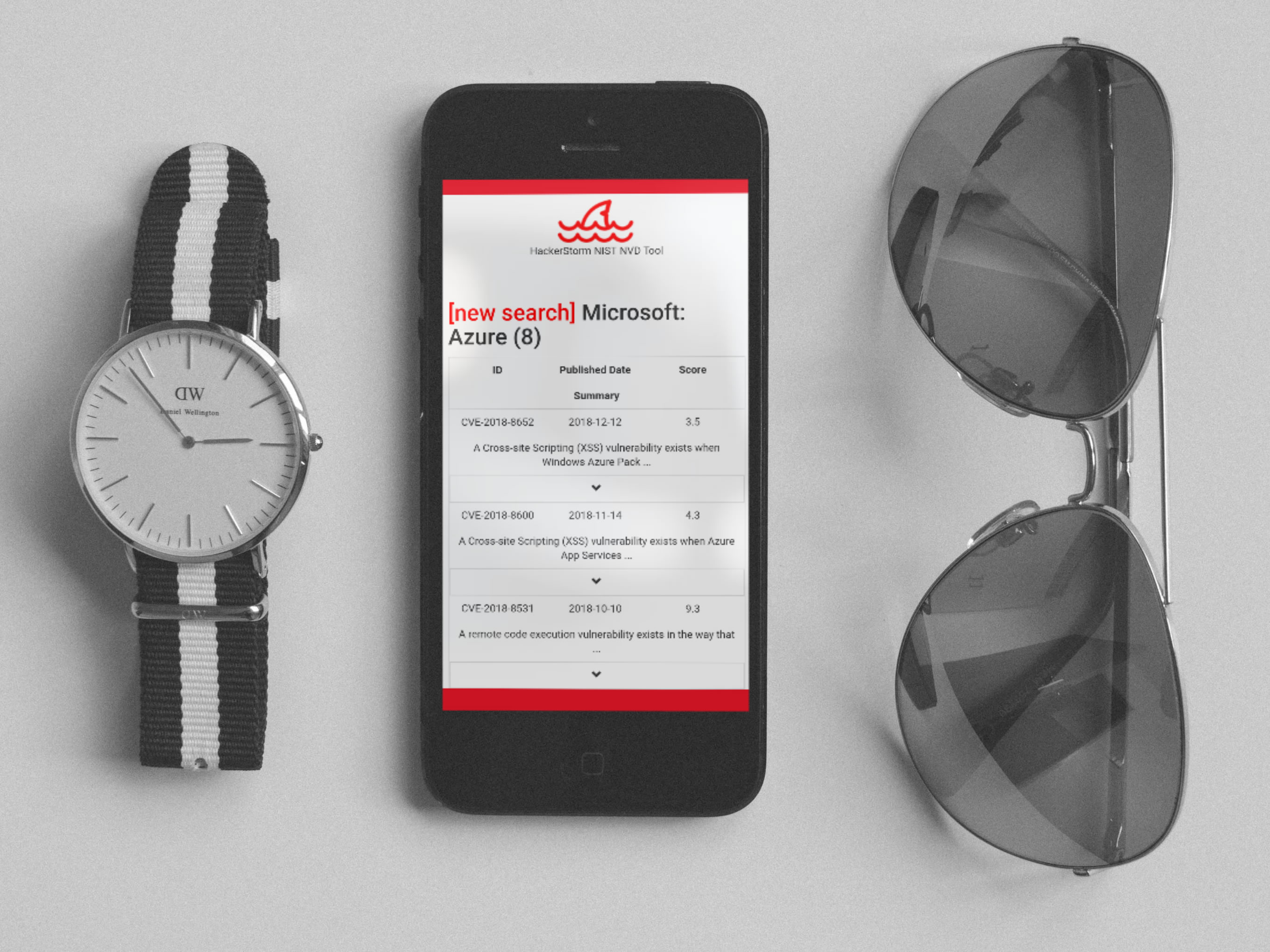
HackerStorm NIST NVD App (beta)
Download our NIST NVD App
Lookup vulnerabilities for thousands of vendors on the go via your smart device.
More infographics coming soon, please check back or follow us on Twitter for updates @hackerstorm
News & Advisories
Free Apps
Threat Research
Other links
© 2003-2019 Hackerstorm.co.uk. All rights reserved
Free Stuff !
We have Cyber security news and a vulnerability search app. We also have a bunch of infographics describing threats and some How To Guides. Scroll down to download everything.
Cyber Security News App

NIST NVD Search App

Cyber Threats Infographics

How To Infographic Guides
